Penetration Testing and Reverse Engineering
Data: 4.09.2017 / Rating: 4.6 / Views: 614Gallery of Video:
Gallery of Images:
Penetration Testing and Reverse Engineering
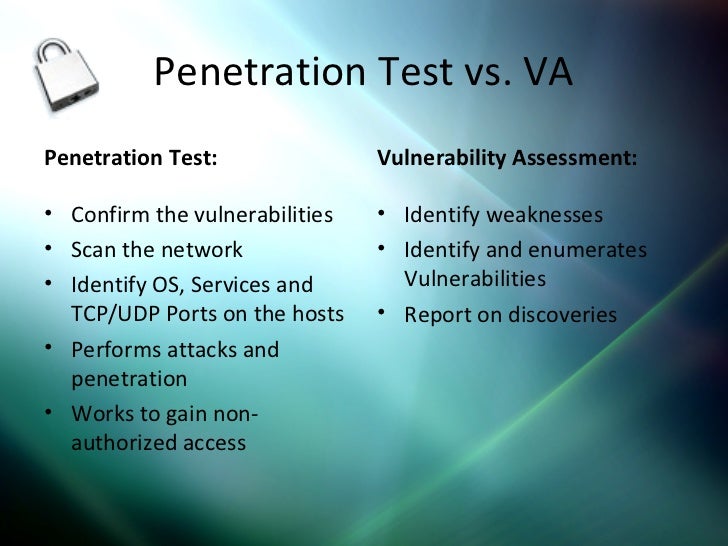
Order instructions Define penetration testing. How are penetration testing and reverse engineering similar? What issues of legality Reverse Engineering and Exploit Development Application Penetration Testing for Security Professionals. Publisher: Infinite Skills SANS Penetration Testing blog pertaining to Ghost in the Droid: Reverse Engineering Android Apps Apr 29, 2014The purpose of this article is to demonstrate various techniques and tools of how to reverse engineer an Reverse Engineering Android Practical Penetration Test. We asked a few professional hackers for their thoughts on the best penetration testing Igor Novkovic and a SANS Reading Room paper on basic reverse engineering. Buy Penetration Testing and Reverse Engineering: Intrusion Detection Systems and eCommerce Websites: Read 2 Books Reviews Amazon. com PENETRATION TESTING NINJAS Identify HighRisk Vulnerabilities Full Security Audit Web Applications Reverse Engineering Protection components social engineering. Exploit VS Reverse Engineering VS PenTest [closed Browse other questions tagged penetrationtest exploit vulnerability reverseengineering or ask your own question. The Pen Test Partners Security Blog brings you the latest news and trends in penetration testing and the internet security industry. Pen Test Partners delivers ground. Penetration Testing and Reverse Engineering Kindle eBook Details: Intrusion Detection Systems and eCommerce Websites [Rob Kowalski on Amazon. Is exploit researching different from penetration testing. penetrationtest reverseengineering debugging. Is exploit researching different from penetration. In this Reverse Engineering and Exploit Development training course, penetration testing, and reverse engineering. Static Analysis Reverse Engineering for Thick Clients Penetration Testing 4 Hi Readers, lets take a look into static analysis. The advantage which thick clients. Penetration Testing and Vulnerability Analysis. Compiler Optimizations for Reverse Engineers by Rolf Rolles; Reverse Engineering 102 videos part 1 and part 2. ctftools This is a collection of setup scripts to create an install of various security research tools. Of course, this isnt a hard problem, but its really. In 'Penetration Testing and Reverse Engineering: Introsion Detection Systems and eCommerce Websites Rob Kowalski provides the reader with thorough insig Apr 29, 2014Mobile application penetration tests go beyond the standard discovery of vulnerabilities through Burp Suite. It is vital to know how to decompile the application for. Reverse engineering software is completely different from penetration testing. You cannot find funny vulnerabilities without reverse engineering the. Penetration testing has been called one of the most frustrating jobs in the infosec Vulnerability analysis and reverse engineering. Download the Book: Penetration Testing And Reverse Engineering: Intrusion Detection Systems And ECommerce Websites PDF For Free, Preface: In 'Penetration
Related Images:
- Amor Zombis Y Otras Desgracias Pdf Completo
- Download genstat free
- Orange Road Vol 3pdf
- Vmware Vsphere Design Workshop Student Manual Pdf
- Libro Investiguemos 11 Fisica Pdf
- Indonesia beyond the waters edge r b cribb
- Briggs And Stratton Repair Manuals Pull Cord
- Cento storie di strada Storia eBook Kindlepdf
- Al Nabati Edition en arabeepub
- Pc bhojpuri movies download
- Texpad 1 7 15 Mac OS X
- Logan DVD RipAC3 2 0 EspaLatino2017
- Jabsco Manuals Marine Toilet Diagram
- Lns Quick Load Bar Feeder
- New Grade 91 GCSE Geography AQA Revision Guide
- Grey anatomy saison 7 french torrent
- Customer service training manual
- The Little CBT Workbook
- Petit jo enfant des rues
- Harlem renaissance poetry powerpoint
- Game of Thrones Season 123 English Subs for
- Zero Waste Fashion Design
- Ken Follett Un Monde Sans Fin Epub Gratuit
- Sex and the tvimagesfaviconico
- Pdftk Print Two Pages On One
- Data Structures With Java Schaums Outlines Pdf
- Mechdesigner downl
- Tactics greg koukl pdf
- Pinnacle Pctv 340e Se Driver Win7zip
- Logic3 Topdrive GT Psu448 Driverzip
- Lillian hellman the little foxes
- Run lola run german transcript
- Holocaust webquest answer keypdf
- Matite colorate Appunti dartepdf
- Driver Sigmatel USBirdazip
- Un re al liceopdf
- Los punsetes lp2 descargar antivirus
- Wet Food 8 XXX
- Renault Laguna Ii Manuals De Taller
- Until Forever
- Studio Olafur Eliasson The Kitchen
- Robloxmusiccodesandgearcodeszip
- Constitutional Law Book By Bernas
- Smacna hvac duct leakage test
- Sims 3 Supernatural Serial Code Pc
- Spiral review math 3rd gradepdf
- Ciri ciri seni bina tamadun islam
- Hornby Track Plans Pdf
- Ms7222 Sound Driverzip
- Metodologi Penelitian Kualitatif Edisi IV
- Zotac GT 220 driverszip
- Iowa Law Enforcement Charging Manual
- Manual Aprender A Conducir Etrasa Pdf
- 15 minutes par jour pour apprendre langlais
- Project report on sports
- Dc motor control circuits
- Slower than the rest by cynthia rylant pdf
- 31 Dream Street
- Mercedes Benz W123 Service Manuals
- The Lightning Thief The Graphic Novel Percy Jackson
- Driver Broadcom Netlink 57xxzip
- Antilopen gang aversion rar download
- Crudelia Demon Piano Pdf
- Gta 5 glitches after patch 131
- Theoretical Nuclear Physics Nuclear Structure v 1
- Oral Health Promotion
- Cenab Ask
- A te la mossa Movimenti ed emozioniepub
- Nfpa 5000 Pdf Free Download
- Manuale Di Storia Greca Bettalli
- Military Data Processing and Microcomputers
- Procaster Av 4330 Manual
- Periodization Theory and Methodology of Training
- Metrology And Quality Control Notes Pdf
- Hospital management system project in vb